Is Samsung intentionally shipping laptops with keylogger/spy software?
Updated: 2011-03-31 00:15:16
 Network World reported today that Samsung may be shipping some new laptops with a keylogger pre-installed. When the customer contacted Samsung tech support they acknowledged its presence after much questioning. Read more…
Network World reported today that Samsung may be shipping some new laptops with a keylogger pre-installed. When the customer contacted Samsung tech support they acknowledged its presence after much questioning. Read more…
 US National Public Radio reports today that BP's Gulf oil spill woes - which already include paying out compensation amounting to a whopping $4B - have been worsened by a data spill.
Just one lost laptop caused all the trouble.
Read more…
US National Public Radio reports today that BP's Gulf oil spill woes - which already include paying out compensation amounting to a whopping $4B - have been worsened by a data spill.
Just one lost laptop caused all the trouble.
Read more…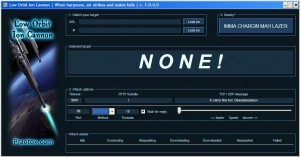 So, last night I downloaded a version of the Low-Orbit Ion Cannon, the traffic generation tool which Anonymous has been using to attack various websites. The version I acquired, from SourceForge, was not one which had been modified for use by Anonymous – it didn’t have the “Hive” function which allows it to be utilized [...]
So, last night I downloaded a version of the Low-Orbit Ion Cannon, the traffic generation tool which Anonymous has been using to attack various websites. The version I acquired, from SourceForge, was not one which had been modified for use by Anonymous – it didn’t have the “Hive” function which allows it to be utilized [...] Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive March 2011 40 February 2011 37 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 283 Corporate 192 Enterprise 327 McAfee Labs 1058 Tags 1 million guarantee access to live fraud resolution agents Acquisition Channel Partners Compliance Consumer counter identity theft credit card fraud and protection credit fraud alerts credit monitoring and resolution critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security encryption Endpoint Protection enterprise facebook Family
Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive March 2011 40 February 2011 37 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 283 Corporate 192 Enterprise 327 McAfee Labs 1058 Tags 1 million guarantee access to live fraud resolution agents Acquisition Channel Partners Compliance Consumer counter identity theft credit card fraud and protection credit fraud alerts credit monitoring and resolution critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security encryption Endpoint Protection enterprise facebook Family Larry Magid's open letter to teen age bloggers - and their parents
Larry Magid's open letter to teen age bloggers - and their parents Take a few minutes to share your experiences in teaching your kids Internet Safety -
and check out what other parents have done
Take a few minutes to share your experiences in teaching your kids Internet Safety -
and check out what other parents have done Internet safety policies and practical guidelines to help make the Internet safer for children and their families.
Internet safety policies and practical guidelines to help make the Internet safer for children and their families. Vital Security Tools and Tips to Secure Your Computers - Guard Against Fraud and ID theft - includes PC Safety book plus free Resale Rights
Vital Security Tools and Tips to Secure Your Computers - Guard Against Fraud and ID theft - includes PC Safety book plus free Resale Rights A Library of Free Internet Security Articles and Computer Safety Articles and Reports on Maintaining Your Computer Protection against adware, spyware, vituses and trojan horses
A Library of Free Internet Security Articles and Computer Safety Articles and Reports on Maintaining Your Computer Protection against adware, spyware, vituses and trojan horses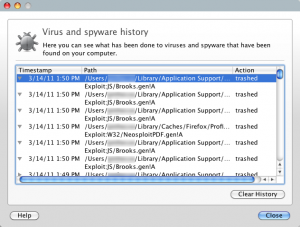 Yesterday, I started getting a bunch of warnings from the anti-virus program I’ve got installed on my Mac – F-Secure Mac Protection Technology Preview. Since I wasn’t doing anything out of the ordinary or perform any “suspicious” behavior, this was a surprise to me. (Especially considering I had only received one virus alert from the [...]
Yesterday, I started getting a bunch of warnings from the anti-virus program I’ve got installed on my Mac – F-Secure Mac Protection Technology Preview. Since I wasn’t doing anything out of the ordinary or perform any “suspicious” behavior, this was a surprise to me. (Especially considering I had only received one virus alert from the [...] How do you know which ciphers your SSL service supports? The best way to find out is to ask, and that’s exactly what SSLScan does. SSLScan is a command-line tool that, given an address and port, will generate a long list of ciphers and report whether the SSL service at the location accepted or rejected [...]
How do you know which ciphers your SSL service supports? The best way to find out is to ask, and that’s exactly what SSLScan does. SSLScan is a command-line tool that, given an address and port, will generate a long list of ciphers and report whether the SSL service at the location accepted or rejected [...] Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive March 2011 26 February 2011 37 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 276 Corporate 191 Enterprise 326 McAfee Labs 1056 Tags Acquisition Channel Partners Compliance Consumer counter identity theft critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security encryption Endpoint Protection enterprise facebook Family Safety global threat intelligence google government identity protection identity theft lost wallet protection malware McAfee McAfee Identity
Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive March 2011 26 February 2011 37 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 276 Corporate 191 Enterprise 326 McAfee Labs 1056 Tags Acquisition Channel Partners Compliance Consumer counter identity theft critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security encryption Endpoint Protection enterprise facebook Family Safety global threat intelligence google government identity protection identity theft lost wallet protection malware McAfee McAfee Identity